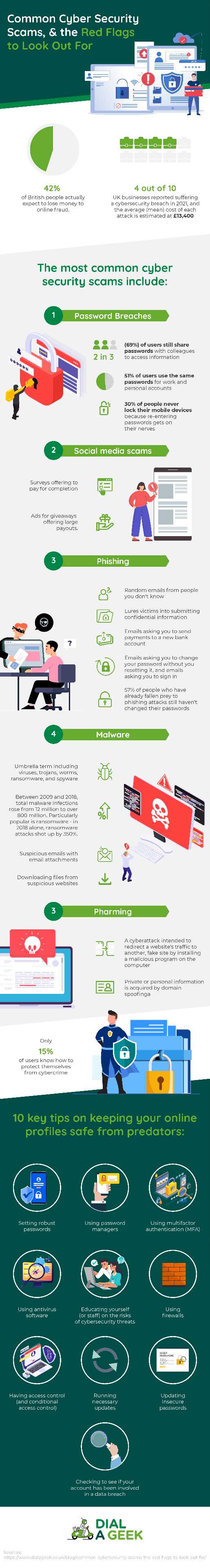
A UK Cyber Survey found that 42% of British people actually expect to lose money to online fraud. With this shocking statistic in mind, we asked our founder (and Chief Geek) Gildas Jones all about cybersecurity scams covering the most common and most unexpected red flags that consumers and businesses alike should keep an eye out for, and giving advice on how to keep their online profiles safe from predators. Read on to find out more…
Click the image to enlarge the infographic…
Share this Image On Your Site
—
Most Common Cybersecurity Scams
According to recent studies, 4 out of 10 UK businesses reported suffering a cybersecurity breach in 2021, and the average (mean) cost of each attack is estimated at £13,400. Below are a few of the most prevalent cybersecurity scams:
Password Breaches
- Impacts consumers and businesses
Recent studies found that two in three (69%) of users still share passwords with colleagues to access information, and over half (51%) of users use the same passwords for work and personal accounts. An NCSC survey also revealed that 30% of people never lock their mobile devices because re-entering passwords gets on their nerves. With these stats in mind, it’s no wonder that password breaches are rampant and one of the most common cybersecurity scams out there.
If you are worried that your passwords are at risk, there are free resources, such as HaveIBeenPwned, which help you quickly assess if an online account has been compromised or “pwned” in a data breach.
Social media scams
- Impacts consumers
Social media scams are meant to harvest data from you to sell to third parties. A few examples of red flags include surveys offering to pay for completion, and ads for giveaways offering large payouts.
Phishing
- Impacts consumers and businesses
Recently, there have been huge increases in phishing attacks (now the most “effective” threat). Phishing is, simply put, a scam. It’s a type of social engineering that manipulates users into revealing personal and confidential information. Hackers generally send a spoofed email with a legitimate source name to trick the victim into clicking on the malicious link or attachment. Some phishing emails could also appear to come from within your organisation.
Phishing remains the top social engineering scam that lures victims into submitting confidential information – however, whilst phishing can be easily carried out it can also be easily identified.
A few examples of phishing red flags include random emails from people you don’t know, emails asking you to send payments to a new bank account, emails asking you to change your password without you resetting it, and emails asking you to sign in.
Shockingly, 57% of people who have already fallen prey to phishing attacks still haven’t changed their passwords, so phishing and password breaches somewhat go hand-in-hand.
Types of phishing include:
Malware
- Impacts consumers and businesses
Malware is an umbrella term including viruses, trojans, worms, ransomware, and spyware. Its main goal is to disrupt the system or steal sensitive information. Its main goal is to disrupt the system or steal sensitive information – and it’s on the rise. Between 2009 and 2018, total malware infections rose from 12 million to over 800 million. Particularly popular is ransomware – in 2018 alone, ransomware attacks shot up by 350%.
A few examples of red flags include suspicious emails with email attachments, downloading files from suspicious websites, and outdated computer systems.
Pharming
- Impacts consumers and businesses
Different to phishing, pharming is a cyberattack intended to redirect a website’s traffic to another, fake site by installing a malicious program on the computer. Pharming can be conducted either by changing the hosts file on a victim’s computer or by exploitation of a vulnerability in DNS server software. Pharming is trickier than phishing since it launches an attack at the DNS level, making it difficult to spot.
The main differences between phishing and pharming include:
| PHISHING | PHARMING |
| The attackers seek crucial information by legal electronic communication | A more technical and advanced method is used to acquire credentials. |
| Uses baits, like fake links | Negotiates on the DNS server to redirect users to a simulated website |
| Uses data theft techniques (e.g. smishing, fax phishing, and vishing) that caused many organisations to suffer | Uses techniques like DNS hijacking, DNS cache poisoning, and DNS spoofing |
| One person is scammed at a time through a test or email | A link is forged which redirects the user from one website to another which is fake and looks like |
| The victims are tricked by providing personal mail or message | Private or personal information is acquired by domain spoofing |
More Unexpected Cybersecurity Scams
The major trends in cybersecurity are tied to the growing sophistication of the threats out there and the way the workplace of today is different to that of a few years ago.
For example, there are now more remote endpoints to track (laptops and other devices from home workers), and there is an increased difficulty of hardware and software updates in distributed workplaces. Also, larger businesses especially are ignoring the dangers of no-longer supported software. Below are some of the more unexpected, but rising, cybersecurity scams to be aware of:
Man in the Middle Attack (MITM)
- Impacts businesses
A man in the middle (MITM) attack is a general term for when a perpetrator positions themself in a conversation between a user and an application—either to eavesdrop or to impersonate one of the parties, making it appear as if a normal exchange of information is underway. This can also be a business email compromise (BEC), as active eavesdropping, where the attacker has access to the account for a period of time, just waiting to change the back details on an invoice for a new supplier or client.
A few examples of red flags include unsecured network, weak Wi-Fi password, and no multifactor authentication (MFA) or conditional access.
A MITM attack usually follows on from a malware attack or a password dump, where a breached database has been released on the internet.
Social Engineering
- Impacts consumers and businesses
Social engineering is the psychological manipulation of people into performing actions or divulging confidential information. An example of red flags includes phone calls or text messages from unknown people claiming your machine is infected (this could also be an attacker posing as an employee wanting a password reset).
Denial of Service (DOS)
- Impacts businesses
DOS attacks work by flooding systems, servers, and/or networks with traffic to overload resources and bandwidth. This might be for financial, political, or personal reasons, and the result is rendering the system unable to process and fulfil legitimate requests.
In financial cases, the attacker may demand payment to stop the attack, whereas in political attacks the attacker may wish to take down government websites to protest at government actions. However, personal reasons can also come into play – for example, an individual may have a grievance against a company and decide to enact revenge.
Zero-Day Exploit
- Impacts consumers and businesses
A zero-day exploit is when a newly found vulnerability has been exploited for an unknown amount of time prior to discovery by the user, vendor, or developer. time prior to discovery. Information about these exchanges hands for large amounts of money on the dark web before they are discovered. Once these vulnerabilities are discovered a patch (software update) needs to be created and made available (then actually applied).
The bulk of Zero-day attackers jump at the disclosed vulnerability in the small window of time where no solution/preventative measures exist. Once the patch or fix is released, it can take users a while to apply it which leaves an even greater window of time for hackers to exploit the vulnerability.
LinkedIn was a victim of this type of attack in 2021 when the data of 700 million accounts was breached. Thus, preventing zero-day attacks requires constant monitoring, proactive detection, and agile threat management practices.
Attacks on Internet of Things (IoT)
- Impacts consumers and businesses
While internet connectivity across almost every imaginable device creates convenience and ease for individuals, it also presents a growing—almost unlimited—number of access points for attackers to exploit and wreak havoc. The interconnectedness of things makes it possible for attackers to breach an entry point and use it as a gate to exploit other devices in the network. This is particularly terrifying when you think about what kind of devices are connected to your home or office network (think air-conditioning, fridges and security alarms)
IoT attacks are becoming more popular due to the rapid growth of IoT devices and (in general) low priority given to embedded security in these devices and their operating systems. In one case when a Vegas casino was attacked, the hacker gained entry via an internet-connected thermometer inside one of the casino’s fish tanks.
An example of a red flag includes outdated software on SMART devices inside the home or business.
Attacks on Industrial Internet of Things (IIoT)
- Impacts consumers and businesses
These attacks on devices such as power grid controllers, remote devices controlled via the network, valves, and pumps. This is becoming an issue for national security as control systems for pipelines or power grids are accessed. The most sophisticated and disclosed example of such attack was Stuxnet – it damaged the Uranium enrichment centrifuges in Iran, increased the spin rate on the centrifuges and caused them to break. This is usually a high-level state sponsored attack (also known as ‘cyber warfare’), but criminal organisations have also been involved.
A few examples of red flags include outdated software, and insecurely configured non-hardened devices, that were never designed to be accessed remotely, ending up on the network.
Risk Factors
The main risk factor of cybersecurity scams is the extraction of personal, sensitive, or other data – financial data (such as email details, valuable intellectual property, names, locations, etc) and passwords are the data types which are most likely to be extracted in a cybersecurity scam. This could be information about your company and its employees, your suppliers, or your clients. This data is valuable to the scammer as they can sell it on to third parties, or otherwise use it for political or commercial gain (such as changing bank details on invoices). Passwords can be used to gain access to the account for a MITM attack (business email compromise).
Cyber-attacks can also result in downtime for the businesses affected if a hacker uses Ransomware to bring your systems down, they will hold all your files hostage until a ransom is paid. The downtime of such attack can be incredibly expensive – and so is the ransom; studies found that 13% of UK organisations ended up paying the hackers!
‘In terms of device specific risks, we have bad news: anything connected to the internet is at risk – even if only from zero-day exploit. The best practice is to review all your home and business devices regularly. Do you still need them? Is the software up to date? For businesses, it’s best to partner up with a Managed Service Provider, like Dial A Geek, that will manage all their IT, including making sure patch updates are done.
Online Safety Tips
The NCSC survey revealed that only 15% of users know how to protect themselves from cybercrime. When it comes to keeping your online profiles safe from predators, we have 10 key tips.
- Setting robust passwords
- Using password managers
- Use multifactor authentication (MFA)
- Using antivirus software
- Staff training
- Using firewalls
- Having access control (and conditional access control)
- Limiting the number of Administrator-level accounts
- Implement single sign on (SSO)
- Running necessary updates
Read on below for more information on each:
Create Robust Passwords
Update insecure passwords (remember to make it longer 12+ characters, as standard) – previous research estimated that a gigantic 23 million account holders are still using 123456 as their password! Also, check to see if your account has been involved in a data breach released on the internet (via HaveIBeenPwned).
For more information, check out our blog post on 5 terrifying password stats that prove your business is at risk.
Use a Password Manager
A study found that 57% of people said they find password management an irritation that stops them doing their jobs, so they don’t bother with it. However, if you follow best practices and have different long unmemorable passwords for every site, password managers can make your life so much easier. Use a password manager for storing, generating, and securely sharing passwords.
Use MFA (Multi Factor Authentication)
Multifactor authentication is really important… if you don’t do anything else, just get this implemented. It’s just a code to an app on your phone, like Google Authenticator to get into your accounts.
Use an Effective Antivirus Software
An antivirus is a software program used to prevent, detect, and eliminate malware and viruses. In a business, this must be an effective antivirus, and centrally managed. Always choose industry-approved software and don’t fall for the free antivirus that gives you a false sense of security
Conduct Staff Training
The chance of your business data being breached by an inside attack is surprisingly high… Most inside attacks are accidental, but sometimes the damage is caused by malicious attackers, deliberately looking to do harm, or make money. Luckily, you can prevent and/or minimise both kinds of attacks, and staff training is one way to approach this issue.
In particular, a lack of phishing awareness training is the weakest link when it comes to businesses being at risk. Phishing is how email accounts are compromised the most, so all staff members should be taught about how to avoid those attacks. Yes, the training is partially about hovering your mouse over a link to check where it takes you to before you click on it; but it’s much more than that. Your IT partner will teach you about all the ways to recognize phishing emails, how to check whether invoices/amended bank details are genuine, and a series of random test phishing emails will be sent to all staff members in order to test their knowledge and avoid future disasters)
Use Firewalls
This is a minimum requirement for all devices and networks. Businesses should have security scanning on their networks too
Have Access Control (and Conditional Access Control)
In a business, ensure only the staff who need to access any data can access it. This includes some unexpected aspects, for example checking that your computers are not left unlocked when an employee is away from their desk so anyone can jump on and see the sensitive information. Conditional access control manages which devices have access to various services and data, setting what the minimum device standard is.
Limit Number of Administrator-level Accounts
Ideally, you shouldn’t be the administrator of your computer. A separate admin account should be created, which will force you (or a potential hacker) to enter admin credentials every time you try to install something’
Implement Single Sign On (SSO)
Leaving accounts open when offboarding staff is a security risk (this was how the North American pipeline was breached in 2021 – with a previous employee’s VPN connection left active and disclosed in a breach’). Single sign on means your business 365 or Google Workspace login gets you and your staff into all the other business apps you use, which makes staff onboarding and offboarding faster.
Run the Updates
Every piece of software needs updating, just ensure you restart and run the updates weekly – in a business this would be centrally monitored and managed by your Managed Service Provider as part of your Cybersecurity Compliance.
—
At Dial A Geek our mission is to help businesses grow with our Managed Services – if you have 10 or more employees and need a trusted partner to manage your IT systems, protect your data, assist you in compliance, and help you grow your business, contact us today.